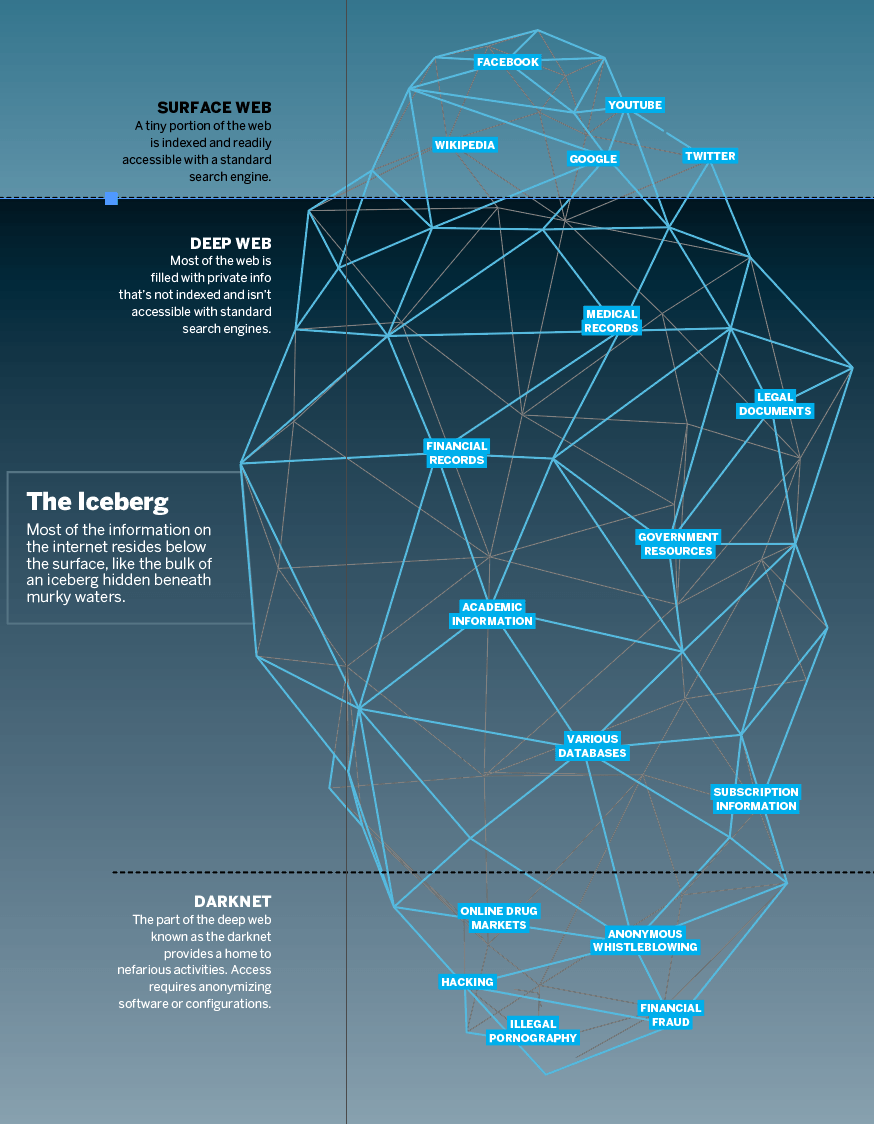
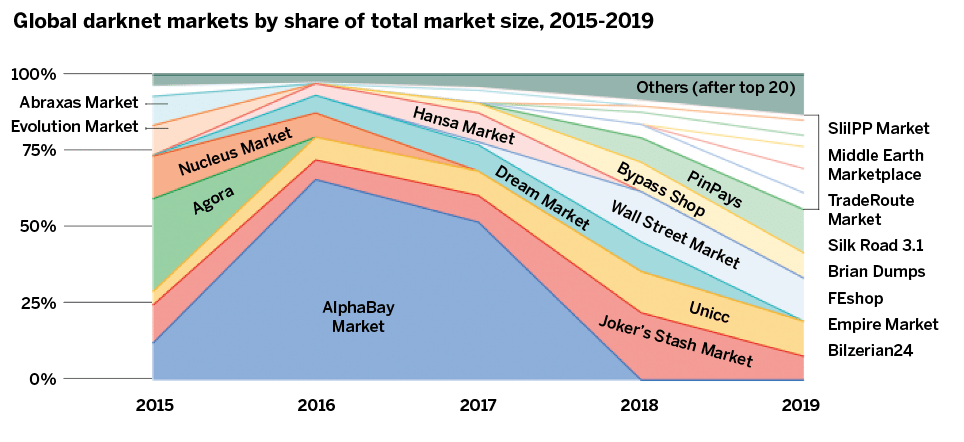
Tracking the Darknet
Are the cops closing in on the criminals who run darknet marketplaces? Luckbox asks the contributors to this issue
Law enforcement agencies are becoming better at tracking down darknet marketeers and closing darknet markets. How are the darknet markets responding?
Eileen Ormsby: The evolution has been interesting. Back in 2012, a highly confidential police memo was leaked to several people on Silk Road that stated law enforcement did not have the technological knowhow to battle the emergence of darknet markets, and their best tools were old-fashioned police work and the dissemination of “FUD”—fear, uncertainty and doubt—among the users. Old-fashioned police work uncovered Ross Ulbricht as the owner of Silk Road and FUD has remained a powerful weapon, but it goes hand-in-hand with increasingly sophisticated cryptocurrency tracing methods. The weak spot for the market owners and large vendors has always been turning crypto into fiat. And law enforcement has been able to follow the money to make arrests as blockchain analysis tools have become more powerful and large crypto exchanges have become more strictly regulated and subject to KYC (Know Your Customer) requirements imposed by the Financial Crimes Enforcement Network.
Jack Rhysider: If you ask former U.S. Attorney General Jeff Sessions, he’ll tell you the authorities are absolutely getting better at tracking and catching darknet criminals. But personally, I believe that you can be anonymous and private online to the point that even the U.S. feds can’t find who you are. People almost always get caught because they slipped up and accidentally leaked information about themselves.
Kim Grauer: We’ve seen that after prominent marketplaces are shut down, vendors relatively easily find other darknet markets on which to sell their wares. As a result, some law enforcement agencies such as the Swedish Police Authority also focus on investigating vendors themselves, and they are having success.
Bitcoin remains one of the most-used cryptocurrencies in darknet markets. Is there any evidence to suggest this trend will change?
Timothy Summers: Bitcoin was the first app for blockchain. And, hey, it’s hard to forget your first app. Bitcoin will continue to be a major driver in the markets—whether darknet or not—regarding cryptocurrencies. However, those in the know are privy to its lack of anonymity and have sought other options. Candidly, there is a direct correlation between the accepted cryptocurrencies and how private the participants believe the exchange needs to be. You may find some people willing to take the risk of using bitcoin, ether, dash, or litecoin; but find more sophisticated groups using monero, Zcash, or PIVX. There is no sign of bitcoin losing ground.
Ormsby: There is no doubt that bitcoin is still king when it comes to darknet market transactions. It has longevity and is comparatively easy to use. However, its strength is also its greatest weakness—the public blockchain means that every transaction is visible to every person.
Some markets are encouraging the use of Monero, an alternative currency that does not have a public blockchain. A couple of newer markets mandate it. Although touted as a privacy coin, Monero does not have the ease of use of bitcoin, and users can lose significant amounts of money as bitcoin is converted to Monero and back again, to cash out.
Darknet “commerce” allegedly includes child pornography, controlled substances, illegal weapons, terrorism and even murder. Do America’s foreign rivals—such as Russia, China, Iran and North Korea—use the darknet to disrupt Western governments or elections?
Summers: There is an abundance of evidence that the darknet is actively used for the exchange of government intelligence, yes, by Russia, China, Iran, North Korea, but also many others. Today, you and I can go on the darknet and purchase a bot army to promote our political agenda to sway an election, and the seller has historical performance data with 5-star reviews.
Grauer: Yes, there are several examples of nation states engaging in illicit activity on both the darknet and clear web to evade sanctions and disrupt democratic elections.

Lazarus Group is an infamous cybercriminal syndicate linked to the North Korean government. Considered an advanced persistent threat by cybersecurity experts, Lazarus is widely believed to be behind the 2014 hack of Sony Pictures and 2017 WannaCry ransomware attacks, as well as a number of cryptocurrency exchange attacks. The U.S. government has reported that North Korea uses funds from exchange hacks and other financial crimes to fund its weapons of mass destruction and ballistic missile programs.
Activities usually associated with Russia and North Korea have also recently been attributed to Iran. And the security firm ClearSky released a report claiming government-backed Iranian hackers have been hacking VPN servers to access large corporate networks.
Interestingly, the Stanford Internet Observatory recently identified the upcoming Taiwanese presidential election as a near-certain target for a Chinese influence campaign.
A Chainalysis report documented an increase in darknet market activity. Yet, press coverage and law enforcement activity appear muted. Why does it seem so quiet out there?
Summers: Law enforcement work is continuing; however, with issues like the coronavirus and the potential of global economic pandamonium, attention is elsewhere. Also, it’s old news that data breaches happen and our data is being sold on the darknet. Truthfully, that doesn’t mean anything real to the everyday person.
Ormsby: It is largely because little newsworthy activity is happening. The fact that you can buy drugs online is old news and it is no more interesting than drug transactions that happen on the street. It’s perhaps less interesting because violence is eliminated from the equation for the buyer and the seller in an online deal, so there will be no tales of shootouts or bloody aftermath of drug deals gone wrong.
Back in 2011 and 2012, Silk Road was novel and outrageous, and it had an enigmatic, idealistic leader who was heavily engaged in the robust and loyal community that grew up around his creation. New markets are simply businesses that have little appeal to journalists.
Rhysider: FBI campaigns like J-CODE and Operation Disarray have recently been announced, which aim to stop the online selling of opium. These campaigns look to be pretty successful with numerous arrests and seizures. But what makes it really hard for the media to cover this is that it’s a constantly changing environment with a lot of secrets. It’s hard to get many answers as to what is going on in the darknet, and that deters the media from talking about it. It’s just too complicated and appears to be a bottomless pit.
More than seven in 10 survey respondents in nine countries said they worry about how tech firms collect and use personal data. So why is the public so slow to adopt the Tor browser and DuckDuckGo search engine—both of which could protect privacy?
Summers: Tor, in its current state, is too slow, complicated as a concept and generally requires too much work for mainstream public adoption. DuckDuckGo is gaining popularity, but it’s fighting against the illusions of openness that companies like Google and others use in their marketing. It’s becoming suspicious to desire privacy on the internet. Usage of Tor and private search engines like DuckDuckGo help us achieve a level of intimacy and privacy that people expect in the physical world and that we should be empowered to achieve in the digital world.
Ormsby: Tor blocks a lot of benign stuff we may want to see because it uses scripts that could compromise our identity in some way. Most of us insist on a fast, simple, intuitive and seamless internet experience, and that’s just not something you’re going to get using the privacy tools, but we accept it because we like the convenience, even while we freak out when our computers seem to be spying on us as ads follow us around the web.