Why You Should Use The Onion Router
The actionable aspects of the darknet begin with embracing its dominant browser
Hardly anything’s all good or all bad, and the roundly criticized anegative side, the darknet’s anonymity provides shelter for criminality of every stripe. But on the positive side, that same anonymity can aid legitimate enterprises by guarding against data breaches and protecting sensitive information from prying eyes.
That’s why internet users—which includes just about everybody—would do well to become familiar with the darknet. To begin that task, let’s review the workings of the internet in general.
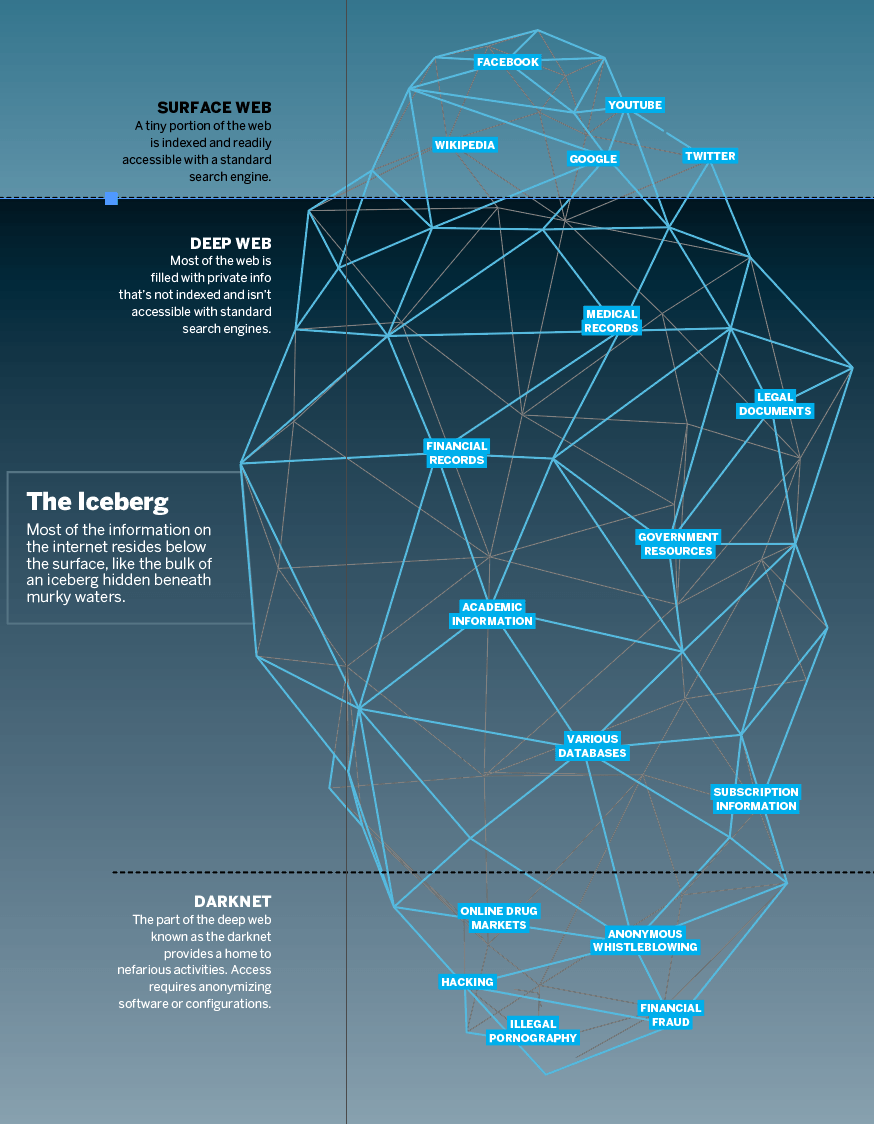
The clear web, or surface web, is what visitors see when they search the internet with a typical browser, like Mozilla Firefox or Google Chrome. It includes the indexed data from search engine titans like Google, Facebook, Amazon and Twitter. It’s all the information available via websites and publicly accessible servers.
It also offers digital content from YouTube, TikTok, Instagram, Netflix and many other emerging digital media channels. But it doesn’t stop there. The clear web also includes data from shopping sites, banks, the Play Store, the App Store, adult sites and any systems that visitors interact with regularly.
Yet, all of that information is at risk on the clear web. When a massive data breach strikes—like the recent attacks on MGM Resorts and Facebook—hackers are using inventive ways to scrape data from websites and servers. It’s like dragging a net across the surface of the ocean. Last year, a whopping 5,183 data breaches exposed 7.9 billion records. That’s a lot of data to drag a net through!
But hackers can’t tap into sites they can’t find, so the anonymity of the darknet could help deflect their attacks. Now, however, a lot of data remains on the surface web.
For perspective, Google processes more than 20 petabytes of data daily, Facebook handles 500 petabytes daily, and Amazon processes somewhere around one exabyte. How much is that in real life? One petabyte is equivalent to 160 million books. An exabyte is 1.6 billion books. In fact, 1.6 billion books stacked upward toward the sky would be just 10,000 miles shy of reaching the moon. Again, that’s a lot of data, and most of it’s available via the clear web. So, why talk about the darknet if all that data’s on the clear web?
Because the clear web accounts for only 4% of what’s on the internet.
Not-so WWW

The deep web, named by computer scientist Michael K. Bergman in 2001, provides a home for non-indexed websites that aren’t registered with search engines. “So, no one can find them!” exclaims Bergman.
Search engines, like Google, use “crawlers” to traverse the internet, adding every site they find to the Google index. But the crawlers cannot reach some places—like behind closed, locked doors on the deep web.
Examples of sites on the deep web include Sci-Hub, which claims to liberate scientific knowledge by offering free research articles; ProPublica, an independent, non-profit Pulitzer Prize winning newsroom; WikiLeaks, a non-profit that publishes information leaks and classified media shared by anonymous sources; and Protonmail, an encrypted email service developed by the European Organization for Nuclear Research, known as CERN.
Moreover, the deep web is simply sites that have not been indexed by a search engine.
Dark versus deep
A small part of the deep web called the darknet consists of thousands of sites that require special tools for access. Stories about the dark web are filled with allegations of sex trafficking, child pornography and drug dealing. Yes, bad guys lurk on the darknet, but it’s more than just criminal masterminds and drug kingpins. In fact, legitimate uses proliferate on the darknet.
Think of the darknet as a place where groups can exchange things in private.
The idea of a hidden web dates back to the beginning of the internet. The Advanced Research Projects Agency Network (ARPANET), created by research universities and the United States Department of Defense, was established in 1969 as the first wide-area packet-switching network with distributed control and the first network to implement the TCP/IP protocol suite. In short, ARPANET was the first version of the internet, and the technology that enabled it still provides the technical foundation of today’s internet.
Myth and rumor still cloud the origins of ARPANET. Some say that it was built as a nuclear-resistant command and control system. Others maintain it was developed to correct the frustrating lack of communication among computers that researchers were using in farflung locations.
Regardless of the original goals, ARPANET was soon ensconced at leading research universities, including Carnegie Mellon University, MIT and Stanford, to name a few. But because ARPANET was government-funded, it was illegal to use it for anything that wasn’t government-related. Just the same, Stanford students sold marijuana to MIT students in the first online transaction.
By the 1980s, the general public could purchase computers and modems to gain access to the new sensation called the internet. But the data from ARPANET and its successors was not publicly accessible because it remained hidden. Over time, the technology evolved, networking expertise became commonplace and people began seeking ways to participate in private exchanges of their own.
Today, anyone with the know-how can create their own private exchange networks on the darknet—and for legitimate reasons.
The darknet goes legit
Accessing the darknet requires special software like the Onion Router, or Tor. It isn’t the only way to reach the darknet, but it’s the most popular. Tor, released in 2002, is free and open source software for anonymous communication. More specifically, Tor directs traffic through a global volunteer overlay network that includes more than 7,000 relays to conceal the user’s location and activity from anyone conducting surveillance.
Tor routes traffic through volunteer relays so that the starting point appears to be somewhere else. For example, Tor may route a message through five different relays in different cities and countries. Because of that level of privacy, it has attracted users ranging from terrorists to the criminal marketplace Silk Road. Like ARPANET, Tor and its underlying technology were funded and developed by the Defense Department for anonymous, private exchange.
Ostensibly, Tor is meant to provide a way to browse privately and freely. It empowers users to block undesired tracking from third-party trackers and ads; defend against unwanted surveillance and monitoring of browsing habits and search history; resist companies fingerprinting them based on browsing habits and device information; and protect data by using multi-layered encryption.
Tor can prove useful for everyone who’s concerned about privacy and private exchange. It has a huge following among journalists seeking to protect sources, activists working to create a movement, cybersecurity experts conducting research and cryptocurrency enthusiasts making transactions. It provides all of those groups the ability to communicate in confidence and be forgotten after each use.
A need for privacy
Debating privacy is as old as mankind. It started with protecting one’s body and domicile and, over the millennia, progressed to maintaining control of personal information. In 1891, Samuel Warren and Louis Brandeis described privacy as the right to be left alone. By 1967, the definition expanded to include the claims of individuals, groups, or institutions to determine for themselves when, how and to what extent information about them is communicated to others.
Many argue in favor of pervasive surveillance, but there’s a legitimate need to oppose government surveillance, notes Edward Snowden, a whistleblower who leaked classified information. “Arguing that you don’t care about the right to privacy because you have nothing to hide is no different than saying you don’t care about free speech because you have nothing to say,” Snowden maintains.
Meanwhile, technology continues to erode privacy. Companies use technology to capture and exploit personal data, the world’s most valuable resource, It’s time for society to re-evaluate whether it’s OK for others to control that information and choose whether to share it with the world.
Everyone should understand the darknet and learn to use Tor. To dive even deeper, consider taking the online courses that teach students to become well-informed Tor users. Do the research and be safe.
For champions of privacy and for those who simply want to be left alone—look to the darknet for a ray of light in the darkness.
Timothy Summers, Ph.D., serves as CEO of Summers & Co., a global strategic advisory firm that provides advice on emerging technology. He’s also the executive director of Cloud and Advanced Network Engineering Services for Arizona State University. @howhackersthink